3 Key advantages Mesh Offers MSPs Over Microsoft 365
It’s one of the most frequently asked questions we hear from MSPs - “why should I use Mesh when my clients have EOP or Microsoft Defender?”
Leaving the detection benefits aside for another day, here are 3 key advantages Mesh offers MSPs over using EOP or Defender from Microsoft.
1 - Message Tracing & Response
Most MSPs receive several tickets each day relating to emails - usually from users who cannot find an email or, whom have received a suspicious email they wish to query with you.
In both scenarios, the MSP response is similar. Login to the client’s tenancy and use the Message Trace function in the Exchange Admin Center, which many find clunky.
On top of this, Message Trace is only available on an individual tenancy. This means there is no cross-tenancy message search or threat hunting. If a new threat has been missed by Microsoft, it is impossible to tell how many other users have received the same/similar threat.
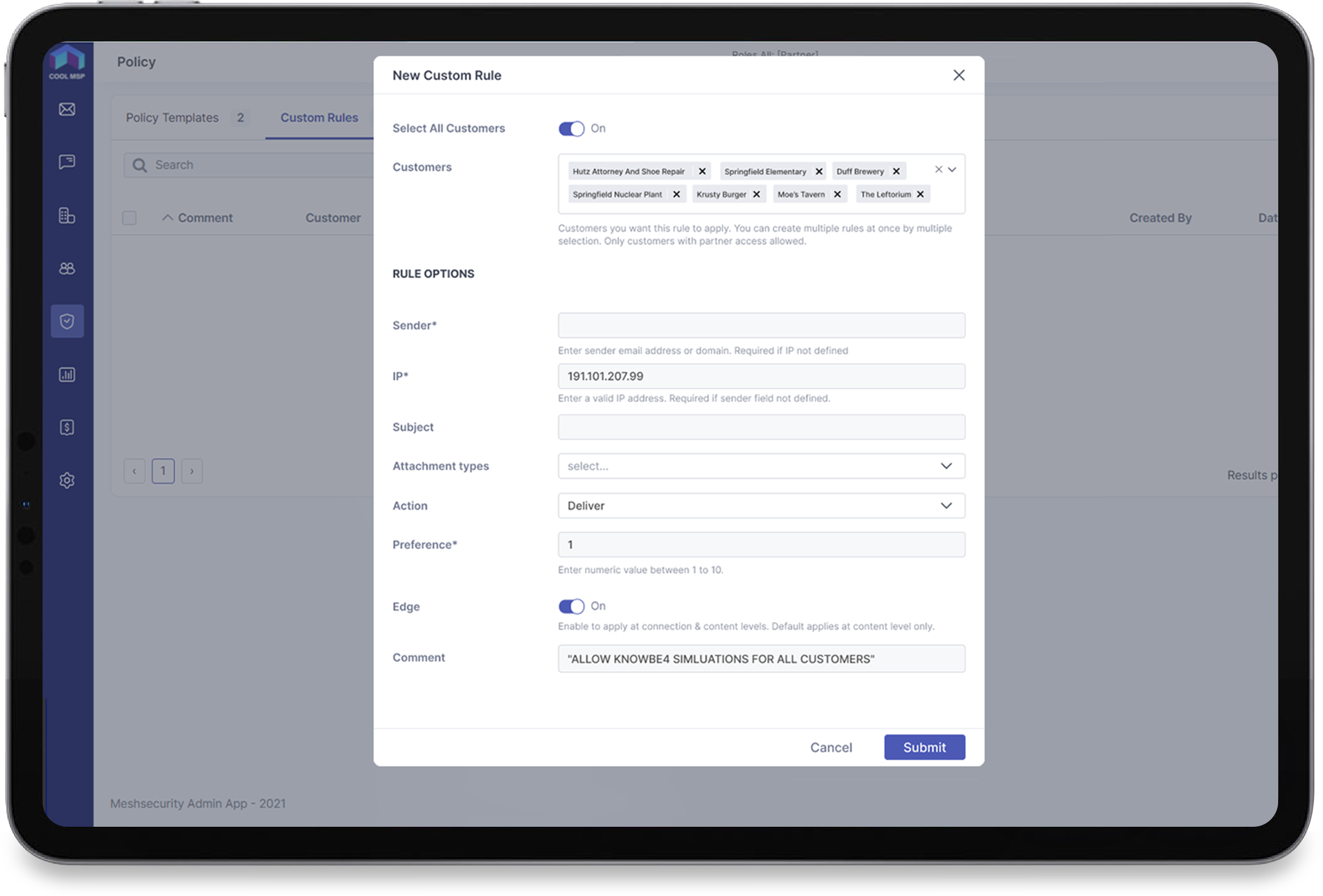
Mesh provides MSPs with unparalleled visibility and control over email traffic to all of their clients in a single location - The Global Live Email Tracker. This enables MSPs to perform advanced searches across all or selected clients based on lots of different search criteria. From the Live Email Tracker, rules can be created for individual recipients, organizations, or even globally across all clients.
2 - Rule Management
Another common task is to create an allow or block rule for a specific sender, domain, or IP address. Again, this involves having to login as the customer and then create the rule locally.
Where this process becomes a lot more arduous is when you want to create this rule for many or all clients. An example of this is when you are implementing a phishing simulation solution, which requires an allow rule for each client in 365. For MSPs with over 100 customers, this will easily take a couple of hours.
Mesh helps MSPs to achieve this within seconds, by facilitating global rules at partner level. Partners can create multi-conditional rules for all selected clients with just a few clicks.
3 - Proof of Value
91% of cyber attacks begin with email - a stat widely used by email security vendors and MSPs. But what visibility do end users have over the efficacy or value of the service you are providing?
Many MSPs will have either a quarterly or monthly business review meeting with their clients in which they leverage metrics and reports to show how their security solutions have been performing.
But what about day to day? And what about reaching every end user instead of just delivering big numbers to your point of contact every 90 days?
Typically with EOP or Defender, end users have no idea as to the amount of dangerous threats or timewasting spam they have been protected from. Most MSPs are missing a trick here, especially those that are providing email protection as part of a cybersecurity bundle, or as a standalone add-on.
If your clients are paying for email security (or even if they’re not), it is important to reinforce the value and significance of this integral part of their cyber protection.
Mesh Quarantine Digests display a quick summary of stats over the last 30 days for each individual user. These digests are fully brandable and are a highly successful way of demonstrating to every single user in your client base that you are keeping them safe from new threats every single day.
As Mesh is exclusively for MSPs, you are free to set their own margins.
Conclusion
Due to Mesh’s uniquely MSP-centric approach, partners are empowered to deliver email security to their clients in a more efficient and comprehensive way. This results in less time spent on management, better informed end-users, and higher margins.
For more information on how Mesh provides MSPs with the ability to manage all clients centrally, from a single pane of glass with unique cross-tenancy capabilities, request a free demo or access to your NFR account today.