A new Variant of CEO Fraud detected By Mesh
Can I get your number?
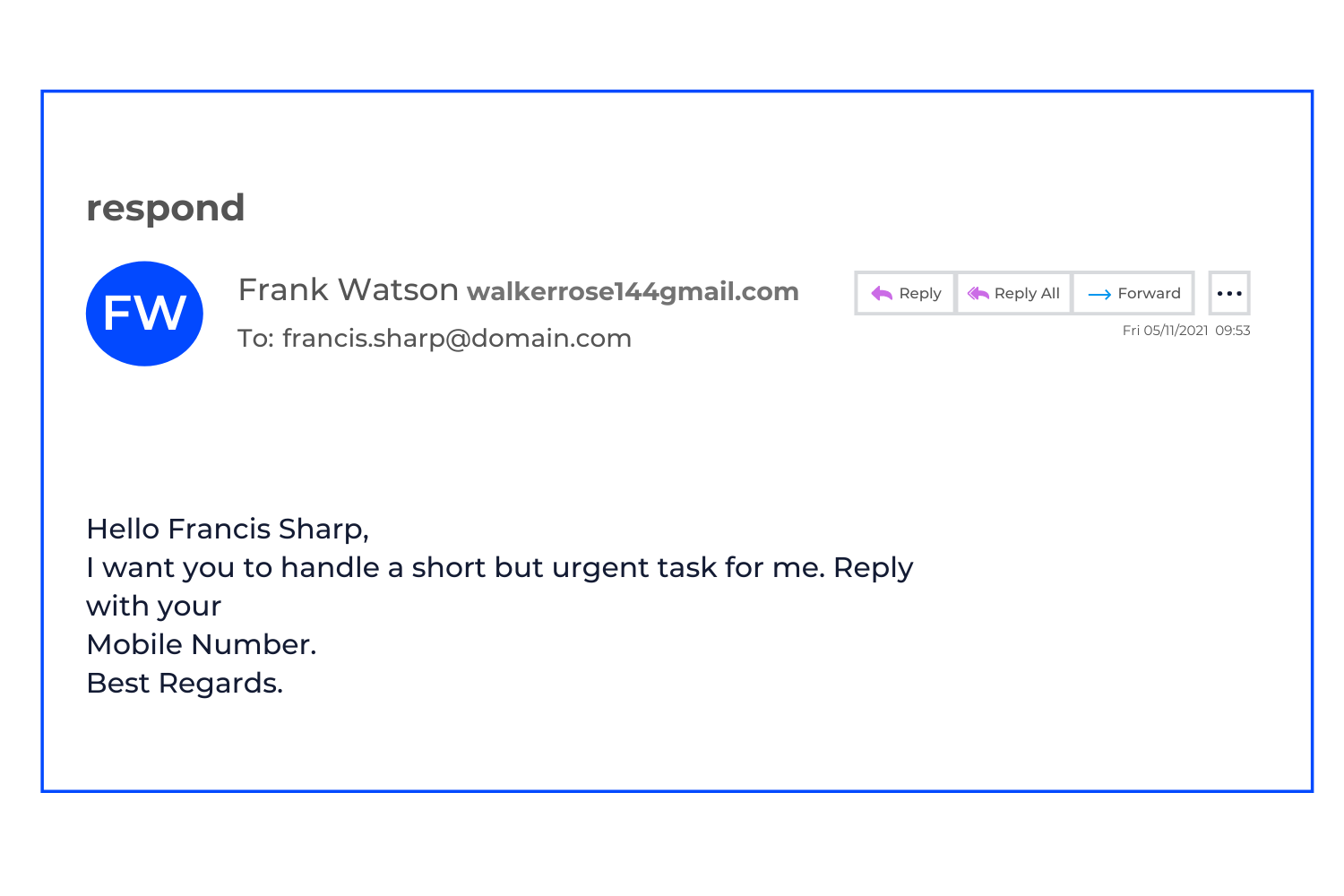
No, this isn’t a pick-up line, this is the latest evolution of CEO Fraud. Last week Mesh observed a significant number of impersonation attacks with a new twist, with two examples shown below. These campaigns utilize Display Name Spoofing and are constantly adapted by attackers attempting to avoid detection.
Historically, CEO Fraud emails contained explicit financial requests like a wire transfer, or asked the recipient to make purchases such as gift cards. As detection capabilities improved, their tactics shifted to more simple requests in the initial email, like - “Hey, are you available now”, or “Hi, I need your help with something urgent”. This style of attack was intended to evade content filters looking for financial keywords and phrases, and initiate the conversation.
This new variant observed several times last week saw a noticeable change in approach, with the attacker looking to take the conversation outside of email immediately by asking for the recipient’s phone number.
Attack Summary
Malware-less, contains no links or attachments
Impersonating the CEO
Using Display Name Spoofing from a Gmail account
Looking to immediately move the conversation out of email
Attack Objective
Avoid detection by email security
Stealing of funds
Identity / credential theft
Access to personal / business assets
*We have used fake names and addresses in both emails but the subject lines and email content is unaltered. These emails were detected by Mesh as Impersonation Attempts on Friday 5th November, 2021.
Conclusion
Although these examples had obvious spelling and grammatical errors, this can actually make detection that little bit harder - as lots of email filters are looking for exact strings and phrases.
This latest variation of CEO Fraud underlines the importance of detecting the very first email in a new campaign and emphasizes the significance of implementing a solution that is continually learning and adapting to new threat types.
For more information on how Mesh protects organizations against CEO Fraud and other forms of impersonation attacks, request a free demo or trial today.