Fake Microsoft Alert Utilized in Credential Harvesting Attack
A new wave of phishing emails are characterized through a highly obfuscated HTML code. These emails do not contain direct URLs in the email body that link to malicious sites. Instead, they employ an attached HTML file designed to redirect users to phishing pages. This technique not only evades basic email security filters due to the complicated structure of the file but also uses the familiarity of the Microsoft brand to help convince end users of its legitimacy.
Microsoft Alert In Credential Phishing Email Attack
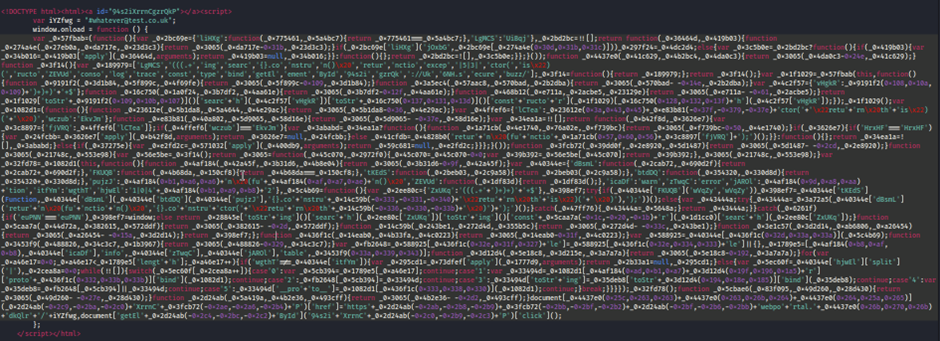
Upon inspection, the HTML attachment reveals code that is heavily obfuscated. This suggests use of advanced phishing kits which are capable of generating unique HTML files tailored to individual recipients. This type of obfuscation complicates the automatic detection and analysis of the malicious intent behind the email.
In this specific scenario, we’ve changed the targeted user’s email address, but the underlying structure of the phishing mechanism remained intact.
Code of the Credential Phishing Email
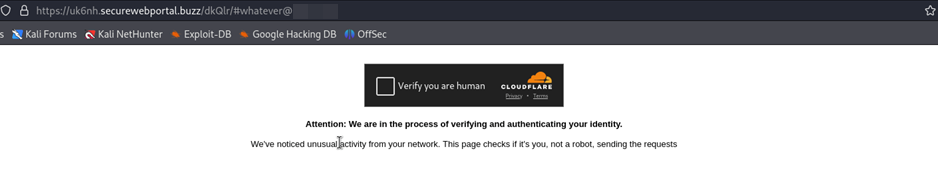
When executed, the user is initially redirected to a CAPTCHA page that requires human verification.
Human Verification within Credential Phishing Email Attack
This indicates that securewebportal[.]buzz is hosted by Cloudflare, which is being abused to facilitate this malicious attack. Once the CAPTCHA is completed, the user is redirected to a fake login page that auto-fills the email address from the compromised HTML file.
At this stage, the collected IP address is cross-checked using a software from using hxxp[://]httpbin[.]org/. This process generates a unique JSON file for each victim. This data is then stored in individual files on the attacker's domain, ensuring precise tracking.
Fake Microsoft Log-In Page in Credential Phishing Email Attack
Further analysis of securewebportal[.]buzz uncovered the following points of interest:
The Microsoft owned images on the landing pages are being hosted on securewebportal[.]buzz rather than fetching them from Microsoft CDN servers.
The exclusion of alternative sign-in options may help end-users that utilise biometric, PIN, or security keys realize the page is not legitimate.
The domain is associated with three separate IP addresses which have been linked to malicious activities such as command and control servers for Cobalt Strike, distribution servers for Android Malware, and malicious PDF files.
These connections underscore the significant threat posed by this domain and highlight the urgent need for heightened security measures. This protection can be provided by Mesh Unified - a holistic email security solution protecting both the perimeter and mailbox.
Mesh Unified utilizes advanced methods to detect hidden threats in HTML attachments and enables Managed Service Providers (MSPs) to protect their customers from such attacks. Click here to learn more about how Mesh Unified can keep your clients’ mailboxes safe.
IOCs:
securewebportal[.]buzz
188.114.96[.]0
188.114.97[.]0
172.64.80[.]1
f0ffd52a37ff12fae16bdbbae11975833341034940e8dea52ae465ef24f7e19b – sha256 of the html attachment